You can register and your instance will be ready in seconds.
Everything you need to develop your project
Api Brew helps you to build your API with just defining their schema.
Declarative API
Easily define and manage your APIs using simple YAML declarations. No need for extensive coding; just specify what you want, and our system handles the rest, turning your declarations into robust API endpoints.
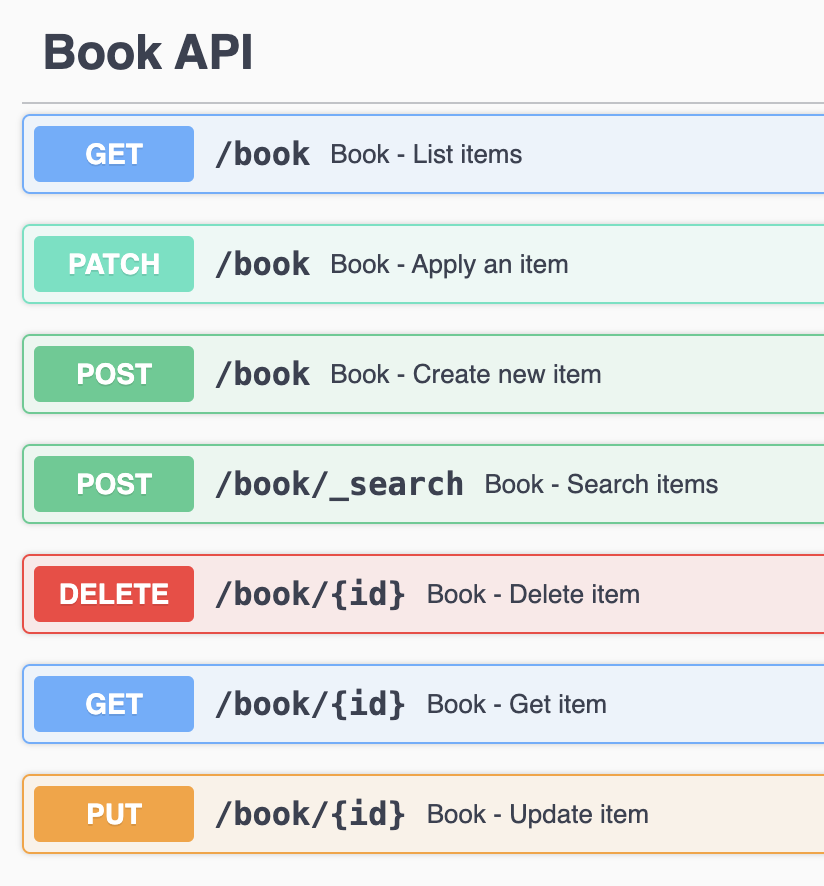
1. Declare book.yml
2. Apply book.yml
apbr apply -f book.yml3. Api is ready with Swagger docs
Nano Code
Introducing a revolutionary way to customize your APIs. With Nano-code, inject snippets of code to modify or extend the behavior of your REST API resources. Tailor your API's behavior without overhauling its structure.
Real Time
Live Mode Interactive: Experience Real-Time Engagement in News and Chat Apps
React code example
const wi = useWatcher(BookEntityInfo, {
filter: {
name: 'Book1'
}
})
const book = useRecord(BookEntityInfo, {
filter: {
name: 'Book1'
}
}, wi)
return <>
Book: {book.name}
<p> {book.description} </p>
</>As result of this code, whenever Book1 is changed on Backend (ApiBrew server) it will notify react and component will be updated on real time.
Language Agnostic Models
Our platform isn't tied to any specific language. Generate models seamlessly for different programming languages, ensuring compatibility and saving development time, regardless of your tech stack.
1. Generate your models for chosen language: [golang, java, typescript, python]
apbr generate --filter name=Book --platform=typescript --path=src/model2. Model is ready
// generated by api-brew
export interface Book {
id: string
name: string
description?: string
author?: Author
version: number
}4. Use your model
const book = {name: 'Book1'}
bookRepository.create(book)Role-Based Access Control (RBAC)
Ensure secure and fine-grained access to your API resources. With RBAC, you can specify who can do what, providing a layered security approach and ensuring only authorized users can access or modify your data.
Api Brew has built-in Role Based Access Control system.
# User
type: system/User
username: joe
password: doe
roles:
- name: test-role
###
# Role
type: system/Role
name: test-role
permissions:
- action: read
namespace: default
resource: book
permit: ALLOWYou can also prepare more complex permissions. e.g. record ownership.
# User
type: system/User
username: joe
password: doe
permissions:
- action: full
namespace: default
resource: book
recordSelector:
equal:
left:
property: owner
right:
value: user1
permit: ALLOW